Digital Literacy, Your Privacy and Data Security

In today's world of digital security and privacy, one simple rule comes to the forefront: the more we know about how technologies work, the better we can protect ourselves. Everything we do online - from messaging to browsing - affects our security. It is crucial to understand how tools like end-to-end encryption, blockchain, VPNs, and encrypted chats work. Additionally, it’s important to comprehend why Telegram makes the decisions it does regarding security and what stands behind those choices.
Digital literacy: conscious data protection
Every day, technology penetrates deeper into our lives, and protecting personal data becomes not just desirable but essential. In today's world, it’s not enough to merely use the internet - you must also know how to counter threats like cyberattacks, phishing, or data breaches. The essence of digital literacy lies not just in using the internet but in understanding how to minimize the risks to your privacy. Passphrases instead of regular passwords, two-factor authentication, VPNs, and privacy settings - these are tools that should be in the arsenal of every literate internet user.
However, data protection isn't just a personal issue. Weak protection of personal information can lead to global problems: from massive data leaks to discrimination based on incorrectly collected or used information. This is a global task that requires everyone's involvement.
Proxy, VPN, TOR: The three pillars of anonymity
When it comes to data protection, Proxy, VPN, and TOR hold leading positions. It’s important not to mix them together, as each of these technologies has its own features and purposes, and their combination may not only complicate the setup process but also reduce the level of security.
So, what are the differences, and how do they work?
Proxy: Simple disguise
A proxy is the invisible bridge between you and the internet. Every time you request something online, the proxy hides your real IP address, allowing you to stay hidden. However, this is only surface-level protection: the proxy doesn’t encrypt traffic, and the server owner can easily reveal your IP. So, if more serious protection is needed, a proxy is just the first step.
VPN: Complete encryption and security
If a proxy is a simple disguise, then a VPN is a fortress. By creating an encrypted tunnel between your device and the server, a VPN hides everything - your IP address and the nature of the transmitted data. It’s the perfect solution for those concerned about their security, whether it’s confidential correspondence or accessing resources with geographic restrictions. But here’s a catch: how much can you trust the VPN provider? In some cases, they may log data, or your information may leak. It's essential to choose reliable providers, such as Ton VPN or Outline VPN.
TOR: Absolute anonymity
If you need maximum privacy, TOR is your choice. Multi-layer encryption, data transmission through dozens of nodes worldwide - all this makes it incredibly difficult to track your activity. Journalists and activists often choose TOR to protect their information. However, anonymity comes with a price: data transfer speed is significantly reduced, and some nodes may be controlled by malicious actors.
Blockchain
Blockchain is not just a technology; it’s a revolution in data security. Imagine a system where each transaction is verified by numerous independent participants (nodes) who keep a strict record of all actions. And here’s where the magic happens: the data becomes almost inviolable. No company or government has full control, making blockchain nearly immune to manipulation. If hackers wanted to alter the data, they would need to hack each node in the network, which is nearly impossible.
Decentralization is blockchain's key advantage. There's no single "ruler" who could control everything. This feature not only protects the system from centralized attacks but also enhances user trust. Your data is securely protected because it resides on multiple independent servers simultaneously. However, like any powerful tool, blockchain has its weak spots - small or insufficiently protected networks may be vulnerable to specific types of attacks.
Cryptocurrencies and privacy
Cryptocurrencies aren’t just numbers in a digital wallet; they are symbols of freedom and anonymity. Every time you make a transaction using cryptocurrency, you’re communicating directly with another user, bypassing intermediaries. In a world where personal data has become the new currency, the ability to store information out of the reach of companies and governments is a breath of fresh air for those who value privacy.
But, as always, there’s a “but.” To effectively use cryptocurrencies, you need to be well-versed in digital security. Ignoring security measures puts you at risk of phishing or fraudulent schemes. Check out our article on fraud types and how you can protect yourself. The blockchain world is full of opportunities, but it requires knowledge and caution.
How does end-to-end encryption (E2EE) work in Telegram?
End-to-end encryption (E2EE) is a true shield that Telegram uses to protect your conversations. Imagine: every message you send is encrypted before it leaves your phone, and only the recipient’s device can decrypt it. Neither hackers, service providers, nor even the platform itself can interfere with your communication.
But there’s a nuance in Telegram - this magic only happens in "Secret Chats." And this is where things get interesting: your messages are not just protected, they aren’t stored in the cloud as they are in regular chats. They’re tied to a specific device - no synchronization between gadgets. Does it seem inconvenient? But it's incredibly secure!
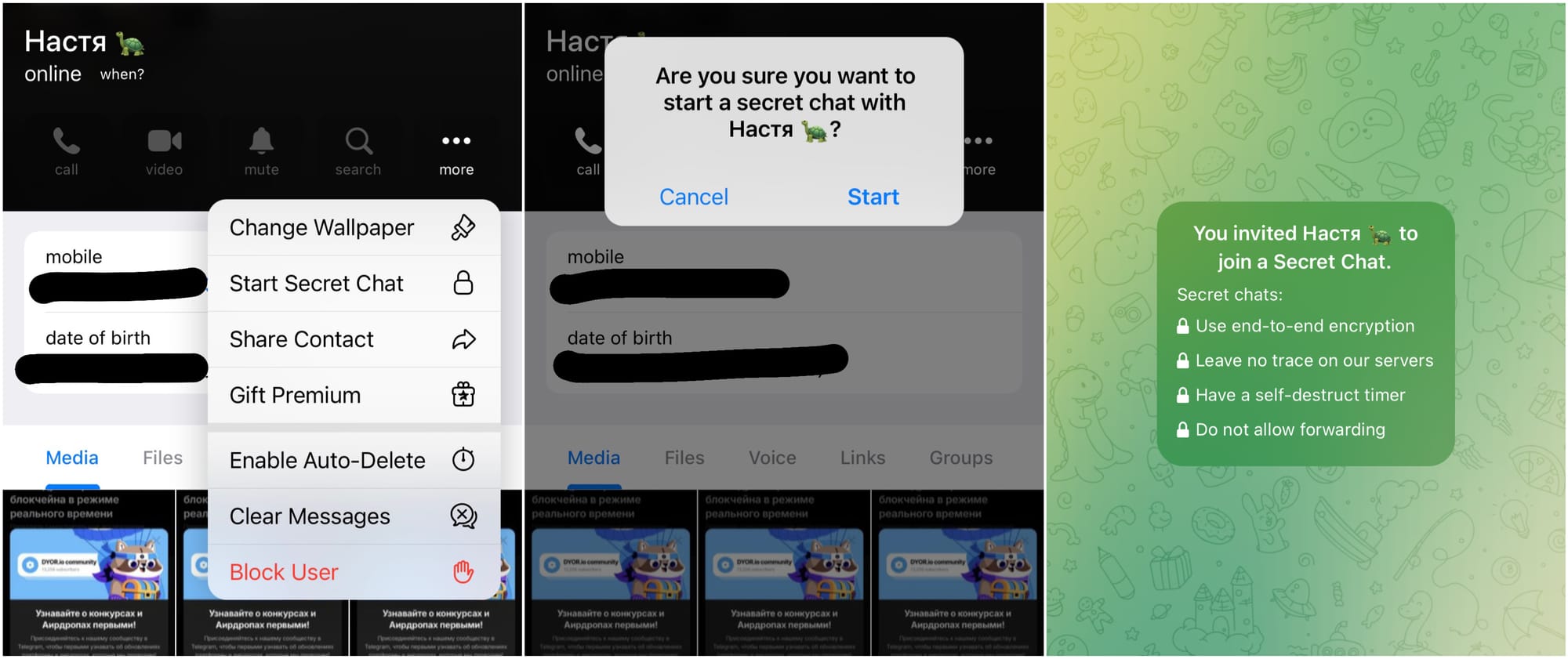
This approach sets Telegram apart from other messengers. The company has chosen complete protection, even if it means sacrificing the convenience of data synchronization. Yes, you might not be able to read secret messages from your tablet, but no one, except you and your conversation partner, will ever know what was discussed.
Why do secret chats work on only one device?
Telegram's secret chats have one crucial feature—they are not synchronized with the cloud, unlike regular chats. Messages are stored exclusively on the devices of the dialogue participants. This approach is chosen to ensure maximum conversation security. If the data were synchronized with the cloud, it would increase the risk of information leakage or hacking. By tying secret chats to just one device, Telegram ensures that as long as your device is under control, no one can access your personal messages.
Challenges with multi-device encryption
Supporting end-to-end encryption on multiple devices is a challenging task, and many other messengers implement it at the expense of weakened security. For example, WhatsApp allows unencrypted chat backups, making them vulnerable to attacks. Telegram took a different path by offering cloud chats for data synchronization and leaving secret chats exclusively for personal and confidential conversations tied to one device.
Key generation and Perfect Forward Secrecy (PFS)
To ensure security, Telegram uses the Diffie-Hellman algorithm for encryption key generation. Every new secret chat generates a unique key known only to the two conversation participants. Additionally, Telegram uses the PFS protocol, which means the keys are regularly replaced after being used for 100 messages or a week. This ensures that even if the current key is compromised, access to old messages is impossible.
Calls in Telegram
Not only messages but also calls in Telegram are protected using end-to-end encryption. The Diffie-Hellman protocol is also used to create a one-time key for calls. During the call, both participants see four random emojis on their screens. The match of these symbols is a sure sign that the connection is secure and no one can eavesdrop. The system uses a library of 333 emojis, creating over 12 billion possible combinations, making a "man-in-the-middle" attack nearly impossible.
Secret chats: More than just E2EE
Secret chats in Telegram offer more than just end-to-end encryption. They come with additional features like self-destructing messages and forwarding prevention. These chats are designed for situations where maximum confidentiality is crucial, making them especially useful for politicians and businesspeople.
Why are secret chats not supported on computers?
One reason secret chats are unavailable in Telegram's web and desktop versions is the need for constant data storage on the device. In desktop applications, all messages are loaded from the cloud and deleted when the session ends. Since secret chats aren’t stored in the cloud, they would be lost upon closing the application.
Cloud chats: A compromise between security and convenience
Although Telegram’s cloud chats don’t use end-to-end encryption, they are still protected. Data is encrypted and distributed across servers in different jurisdictions, making hacking or accessing it very difficult. This approach provides a balance between the convenience of synchronization and data security.
Data protection tools: VoIP, DEA, virtual SIM cards, PGP, and Kleopatra
VoIP: Secure internet calls
VoIP (Voice over Internet Protocol) is a technology that allows you to make calls over the internet, offering a convenient and cost-effective alternative to traditional phone systems. However, it’s not without vulnerabilities, such as the possibility of eavesdropping or phishing attacks. To minimize risks, protection methods like call encryption and VPN use are employed. This helps make connections more secure, preventing data interception. For reliable VoIP operation, it’s recommended to use strong passwords and regularly update security systems.
DEA
Disposable email addresses (DEA) are temporary email addresses that provide privacy protection and convenience when registering on various sites. They’re used for one-time actions or for a limited time, allowing you to easily "disable" the address when necessary.
The main advantage of DEA is protection from spam and data leaks, as your primary email address remains hidden. These addresses are especially useful for registering on platforms with questionable reputations where there’s a risk of ending up on spam lists or encountering cyberattacks.
Some websites and programs offer to generate temporary email addresses for you. For example, AdGuard - an ad blocker and privacy protection tool - provides a free temporary email address generator.
Virtual SIM cards: Mobile communication without a physical SIM chip
Virtual SIM cards (or eSIM) replace physical cards, allowing you to activate mobile communication via software. This solution is especially useful for those who need to manage multiple numbers on one device. Virtual SIM cards help maintain anonymity, as there is no need to use physical cards, reducing the risk of data leakage. Managing numbers through eSIM simplifies the process of switching operators and adds flexibility in using mobile communications.
PGP encryption: A security protocol for email and files
PGP (Pretty Good Privacy) is a powerful tool for encrypting emails and files. It uses a system of public and private keys, making messages accessible only to their recipients. PGP is especially popular among those requiring a high level of protection, such as journalists and activists in censored countries. In addition to email, PGP is excellent for protecting files, making it a universal solution for ensuring data privacy.
Kleopatra: A handy tool for managing PGP
Kleopatra is a program with a simple interface designed for managing PGP encryption. It allows you to create and manage encryption keys, protect documents and emails, and verify digital signatures. Kleopatra simplifies the process of using encryption for those without deep technical knowledge, making it accessible even to beginners.
Conclusion
To sum up, in today's digital world, data protection and privacy are not just options - they are necessities. Modern tools like VPNs, TOR, PGP, and others help not only to maintain privacy but also to ensure your protection when working with digital services.
Even the best technologies can be useless without a competent approach, so the key remains the conscious and knowledgeable use of these tools. It’s important to understand how they work and to be able to use them properly.








